Exploit-Exercises Nebula level00
wargamesThis level requires you to find a Set User ID program that will run as the “flag00” account. You could also find this by carefully looking in top level directories in / for suspicious looking directories.
Alternatively, look at the find man page.
To access this level, log in as level00 with the password of level00.
Key to solving this level is understanding the concept of SUID and GUID. setuid and setgid are represented by s in the user or group permission field. When this mode is flagged on executable file, it will run with the user or group permission of the file instead of the user issuing the command.
We normally use three digit chmod commands where each digit stands for user, group, and others. However, there is another hidden special mode at the beginning of those three digits that is set to 0 by default.
Therefore, by using the find command, we can easily find two files that meets the requirement to capture the flag for this level.
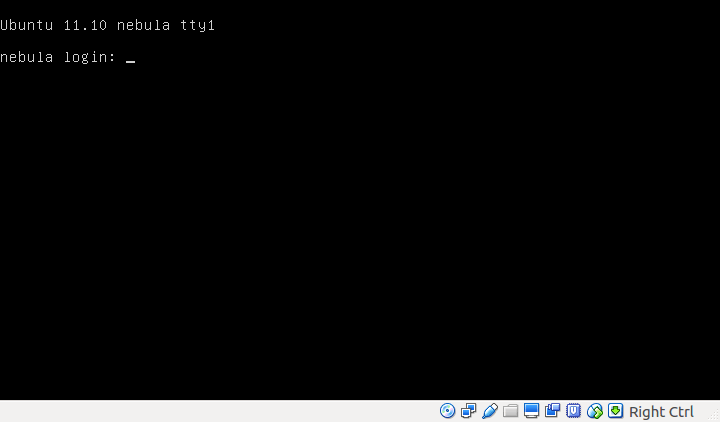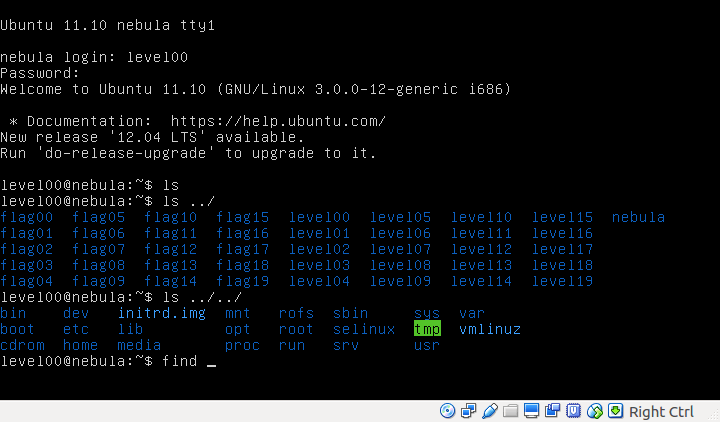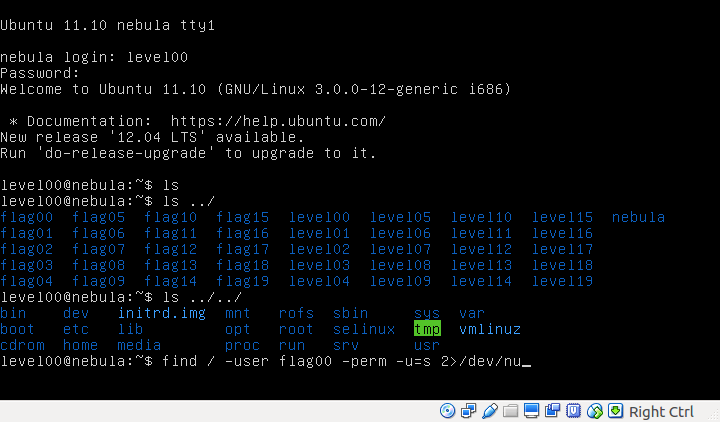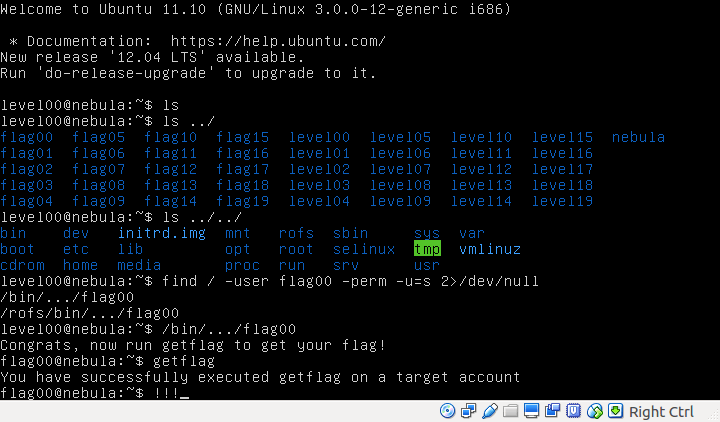
level00@nebula~$ find / -user flag00 -perm -u=s 2>/dev/null
/bin/.../flag00
/rofs/bin/.../flag00
Simply put, I’m running the find command at path = / with conditions where user is flag00 and user permission mode is set to setuid. The last bit of the command just dumps err lines to /dev/null which is a special file that allows you to read and throw it away.
Executing either of the two file found will release the flag.