Exploit-Exercises Nebula level08
wargamesWorld readable files strike again. Check what that user was up to, and use it to log into
flag08account.
To do this level, log in as the
level08account with the passwordlevel08. Files for this level can be found in/home/flag08.
Pcap (Packet Capture) file holds the network activity history. Using the tcpflow command, we will read the pcap file with -r option and output the result to console with -c option.
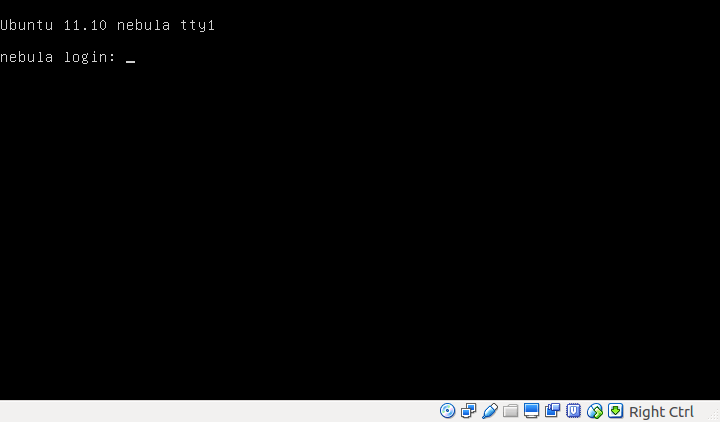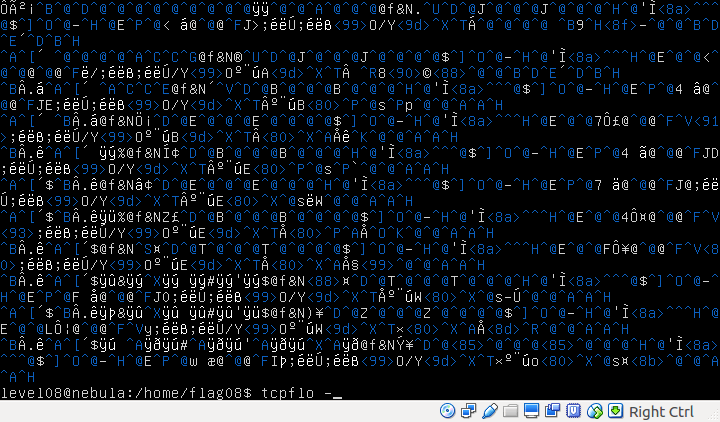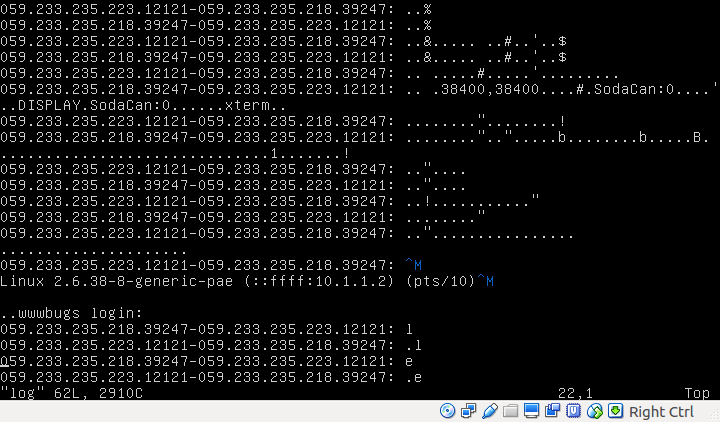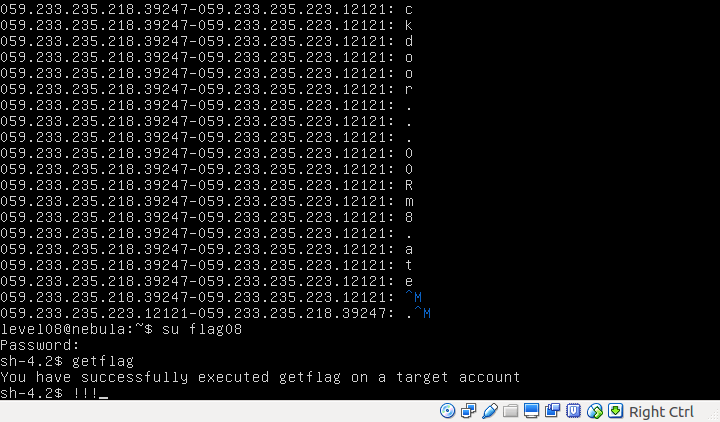
We notice some interesting activity with password input. The user inputs backdoor...00Rm8.ate. I made an assumption that the . represents backspace. So the correct password would be backd00Rmate.