Exploit-Exercises Nebula level09
wargamesThere’s a C
setuidwrapper for some vulnerable PHP code…
To do this level, log in as the
level09account with the passwordlevel09. Files for this level can be found in/home/flag09.
level09.php
<?php
function spam($email)
{
$email = preg_replace("/\./", " dot ", $email);
$email = preg_replace("/@/", " AT ", $email);
return $email;
}
function markup($filename, $use_me)
{
$contents = file_get_contents($filename);
$contents = preg_replace("/(\[email (.*)\])/e", "spam(\"\\2\")", $contents);
$contents = preg_replace("/\[/", "<", $contents);
$contents = preg_replace("/\]/", ">", $contents);
return $contents;
}
$output = markup($argv[1], $argv[2]);
print $output;
?>
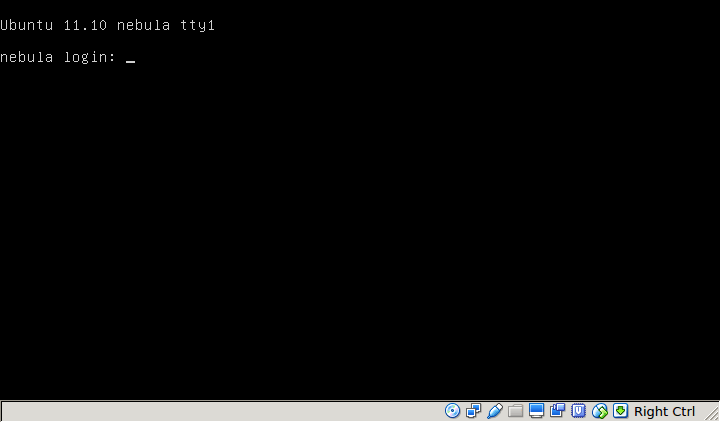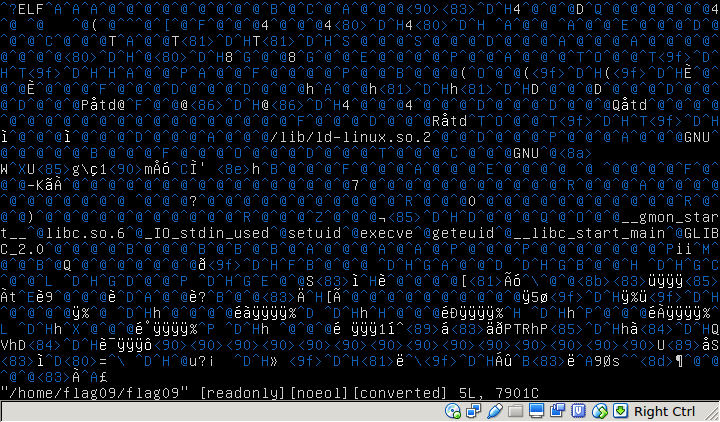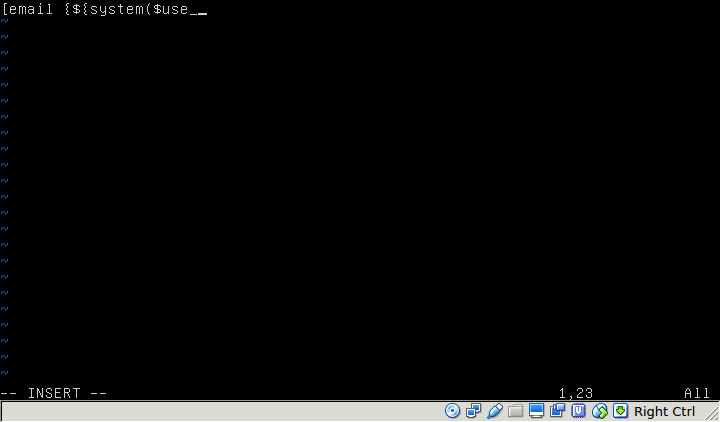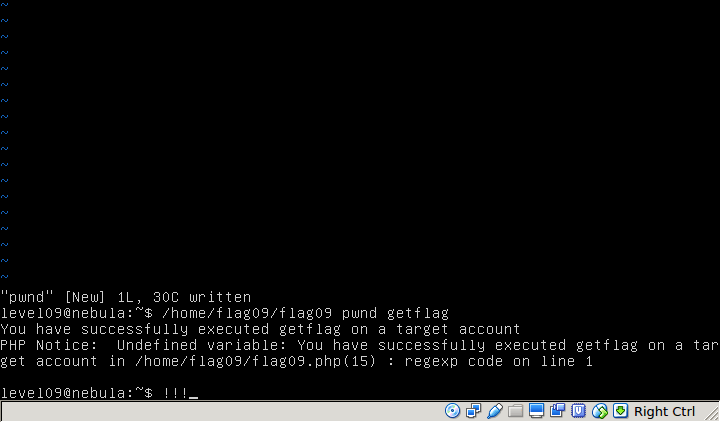
Upon some research, I found out that preg_replace() is not recommended in general because using the -e modifier will allow you to execute the replaced value as PHP code. Looking at the markup function, it is taking the file content of the first argument which later gets called into preg_replace(). I can plant malicious code in $filename, preferably something that will call $use_me as we can pass anything into the second argument (perhaps getflag?).